Standard Access-List Overview
As the name implies, access-lists are sequential listings of guidelines, which are used to provide or prevent the flow of packets within a network based on information provided within the list. Standard IP access lists are very straightforward in the fact that the only criteria used to determine if packets should be ‘permitted’ or ‘denied’ is based solely on the source address of any given packet.
Access-lists may be used for a variety of reasons, including controlling the propagation and reception of routing updates, traffic shaping, definition of traffic that will allow dial backup connectivity, and security. The primary implementation, and the main topic of this lesson, will be to implement the access-list as a security mechanism.
Why implement restricted access?
You may choose to implement security policies for a variety of reasons, which includes, but is certainly not limited to, prevention of outside attacks on company devices, isolation of interdepartmental traffic, or load distribution. Without the use of access-lists all packets within a network are allowed without restriction to all parts of the network.
When using access-lists as a “firewall”, routers can limit or restrict access to your internal network from an outside network, for example the Internet. This type of access-list would typically be placed at the point of connection between the two networks. When using access-lists for interdepartmental isolation, the access-list would typically be placed at strategic locations within the internal network.
The Basics of Standard IP Access-Lists
The basic format of the Standard IP Access-List is:
access-list [#] [permit | deny] [source-address | keyword any] [source mask]
As mentioned earlier, an access-list is a sequential listing of guidelines that are used to provide or prevent the flow of packets. In other words a access-list may contain multiple lines, each following the format as listed above. The access-list may contain multiple lines, specifying multiple source addresses to be evaluated. Each line entry of the access-list must maintain the same access-list number identifier so the router will know that the entities listed will be grouped into the same access-list. Always remember that access-lists are processed “top down”, which means that the first line of the access-list will be check, then the second, etc. The router will immediately break out of processing the access list with the first “match”. Therefore the most general statements should be placed at the beginning of the list to avoid extra processing, more to follow on this.
Various access-lists can be defined by different protocols within a router. The router will know the type of access-list based on the access-list number that is assigned. The numbering range for Standard IP Access-Lists is from 1 to 99. All Standard IP Access-Lists must be numbered within this range.
After a number in the appropriate range has been selected for your access-list, the list must know if the packets to be evaluated will be ‘permitted’ (allowed to pass) or ‘denied’ (dropped and not allowed to pass). This is accomplished by placing either a permit or deny keyword within the line of the access-list. The usage of the keyword instructs the router to allow the packet to pass or not to allow the packet to pass based on the next specified parameter, the source address contained within the evaluated packet.
As briefly discussed earlier, the only criteria used by Standard IP Access-Lists to determine if a packet should be ‘permitted’ or ‘denied’ is based solely on the source address of any given packet. This brings us to the point where we specify exactly which host (or hosts) will be permitted or denied by our access list. This parameter is quite simply, the source ip address of the host that you wish the access-list to take action upon. You may optionally replace the address with the keyword any which will cause the router to act upon “any” ip address.
As found with most all IP addressing schemes, the standard IP access-list allows for a source-mask to be applied to the source ip address. Although similar to the subnet mask that is applied to ip addresses, the source-mask is somewhat different. When using a source-mask with ip access-lists, a bit set to 0 means “match exactly” and a bit set to 1 means “don’t care”. For example, if you would like to include all hosts in the class C network 192.1.1.0, the source address, source mask combination would be: 192.1.1.0 0.0.0.255. This statement says: In the first, second, and third octet of this address (192.1.1), all bits must “match exactly” (0.0.0, or all 0’s in the source-mask for the first, second, and third octet), but we “don’t care” what bits are sent in the fourth octet (255, or all 1’s in the source-mask for the fourth octet). By using this source address / source mask combination a single line in our access list includes all hosts in the 192.1.1.0 network. The keyword any, was briefly mentioned earlier. This keyword is the same as using a source address / source mask combination of 0.0.0.0 255.255.255.255. The 255.255.255.255 source mask indicates we “don’t care” what bits are set in any of the four octets. The use of the source mask parameter is optional. If omitted from the configuration line, the router by default will use a source mask of 0.0.0.0, or “match exactly” the address entered.
We now have the basic building blocks to begin building our first standard IP access-list. There is one more note that is critical to the successful completion of building an access-list. After an access-list has been created, the Cisco router will assume that any source ip addresses that are not explicitly mentioned in the list will be *DENIED*. In other words, at the end of the access-list, the router will implicitly deny all remaining traffic. If your access-list has been configured to permit only a single source-address of 1.1.1.1, ALL OTHER SOURCE ADDRESSES WILL BE IMPLICITLY DENIED.
Creating a simple Standard IP Access-List
Now the time has come to create our first Standard IP Access-list. We will use the format as discussed:
access-list [#] [permit | deny] [source-address | keyword any] [source mask]
Access-lists are created in global configuration mode of the router. Remember that all standard IP access-lists must be numbered in the range of 1-99, for our example we will use #1. We have decided that we want to permit traffic from address 1.1.1.1, and deny all other traffic. The procedure will be as follows:
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#access-list 1 permit 1.1.1.1
Router(config)#^Z
Router#
This configuration creates a permit statement for host address 1.1.1.1. Since the source-mask was not specified, the router uses a default of 0.0.0.0 (match exactly). Don’t forget the implicit “deny any” at the end of the access-list, this automatically denies everything we did not permit.
Applying the Access-list to an interface
Now that we have created out access-list, before the access-list actually does any work it has to be applied to an interface. The interface configuration command for applying the standard ip access-list to an interface is:
ip access-group [access-list-number] [in | out]
Access lists may be applied as either outbound or inbound on the router interfaces. When you apply the access-list as an inbound list, the router will receive an inbound packet, check the source address of the packet against the access list, and either “permit” the packet to be routed to the destination interface if the packet matches a “permit” statement in the access-list, or discard the packet if the packet matches a “deny” statement in the access-list.
When you apply the access-list as an outbound list, the router will receive a packet on an interface, route the packet to the appropriate outbound interface, and then check the source address of the packet against the access-list, and either “permit” the packet to exit the interface if the packet matches a “permit” statement in the access-list, or discard the packet if the packet matches a “deny” statement in the access-list.
To apply the access-list we created above to interface Ethernet 0 as an inbound access-list:
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int Ethernet 0
Router(config-if)#ip access-group 1 in
Router(config-if)#^Z
Router#
To apply the access-list we created above to interface Ethernet 0 as an outbound access-list:
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int Ethernet 0
Router(config-if)#ip access-group 1 out
Router(config-if)#^Z
Router#
Creating a more advanced Standard IP Access-List
Now let’s create a more advanced access list. In this exercise we will create access-list #2, with the following criteria.
Permit all packets originating from network 10.1.1.0 255.255.255.128, but deny all packets originating from network 10.1.1.128 255.255.255.128. We also want to deny all packets originating from network 15.1.1.0 except for packets from a single host of 15.1.1.5. The final criteria is to permit all other traffic not previously mentioned. The procedure will be as follows:
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#access-list 2 deny 10.1.1.128 0.0.0.127
Router(config)#access-list 2 permit 15.1.1.5
Router(config)#access-list 2 deny 15.1.1.0 0.0.0.255
Router(config)#access-list 2 permit any
Router(config)#^Z
Router#
One of the first things you may notice about our configuration is that there is no permit statement for the network 10.1.1.0, which our criteria specified we must permit. The last line of the access-list (access-list 2 permit any) will take care of this criteria. Let’s review our criteria and verify we have completed our tasks:
- Permit all packets originating from network 10.1.1.0 255.255.255.128
The last line of our access list accomplishes this criteria. It was not necessary to explicitly permit this network in our access list since there were no statements in our access-list matching this network except for the final line of “permit any”.
- Deny all packets originating from network 10.1.1.128 255.255.255.128.
The first line of our access list accomplishes this criteria. It is very important to note that it was necessary to use a source-mask of 0.0.0.127 for this network. This mask says we “don’t care” about the final seven bits of the fourth octet, which are the bits have have been assigned for host addressing on this network. The subnet mask specified for the network was 255.255.255.128 which says the first bit of the fourth octet has been assigned to the “subnet” the last seven bits have been assigned for host addressing.
- Deny all packets originating from network 15.1.1.0 except for packets from a single host of 15.1.1.5.
This has been accomplished with lines 2 and three of our access-list. It is very important to note however that the access-list did not accomplish this in the same order as the criteria specified. It is imperative to remember that access-lists are processed top down, and that upon the first match processing stops and action is taken. Our criteria specified to deny packets from network 15.1.1.0 and secondly permit packets from host 15.1.1.5. If lines two and three had been swapped, and the entire network 15.1.1.0 was denied prior to permitting host 15.1.1.5, packets with a source address of 15.1.1.5 would match the more general criteria of “deny 15.1.1.0” first, thus the host would have been denied before it could have been permitted.
- The final criteria is to permit all other traffic not previously mentioned.
The last line of our access list accomplishes this by permitting “any” packets that were not matched in the first three lines of the list.
Bringing it all together
In general the process for creating and implementing standard ip access-lists are:
- Define the rules for which to design the access-list
- Create the access-list with a number in the range of 1-99
- Apply the access-list either inbound or outbound to the appropriate interface
Items 1 and 2 above have been fairly well covered in this lesson. In closing of the lesson one small item still exists for the application of standard ip access-lists. That item is regarding the placement of the access-list. In general standard ip access-lists should be placed nearest the destination and not the source. This is not an absolute rule however and there are exceptions. Due to the fact standard ip access-lists only operate on the source address, detailed granularity is not always possible. Care must be taken to avoid implementing undesirable policies. If a standard access-list is placed near the source it is very possible that access to devices other than those desired will be impeded.
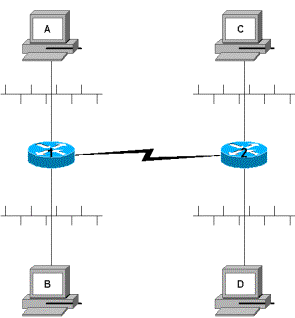
For example, if access-list 2, which we created in this lesson, were implemented as an inbound access-list on the Ethernet interface of a router directly connected to the 15.1.1.0 network, the only workstation that would be allowed off the local segment would be 15.1.1.5. This access-list would most likely be implemented as an outbound access-list on the remote end of the connection, where the filtering of packets is truly desired.
Viewing the figure below, let’s assume that workstation C is device 15.1.1.5, and Workstation D is device 10.1.1.133. Our desire is to implement a policy for Workstation A that only allows Workstation C access from remote Ethernet C. We also wish to implement a policy that will deny any access from remote Ethernet D. Placement is critical for this accomplishment. If access-list 2 from above is implemented as an outbound access-list on Router 2’s serial interface we will accomplish the desired task, BUT we will also deny traffic from Ethernet D to Ethernet B, which is undesired. The same scenario holds true if the access-list is implemented as an inbound access-list on Router 1’s serial interface. If we place this access-list as an outbound access-list on Router 1’s Ethernet A interface, our policy is intact, without any unwanted policy implementations.
|